Login settings screen
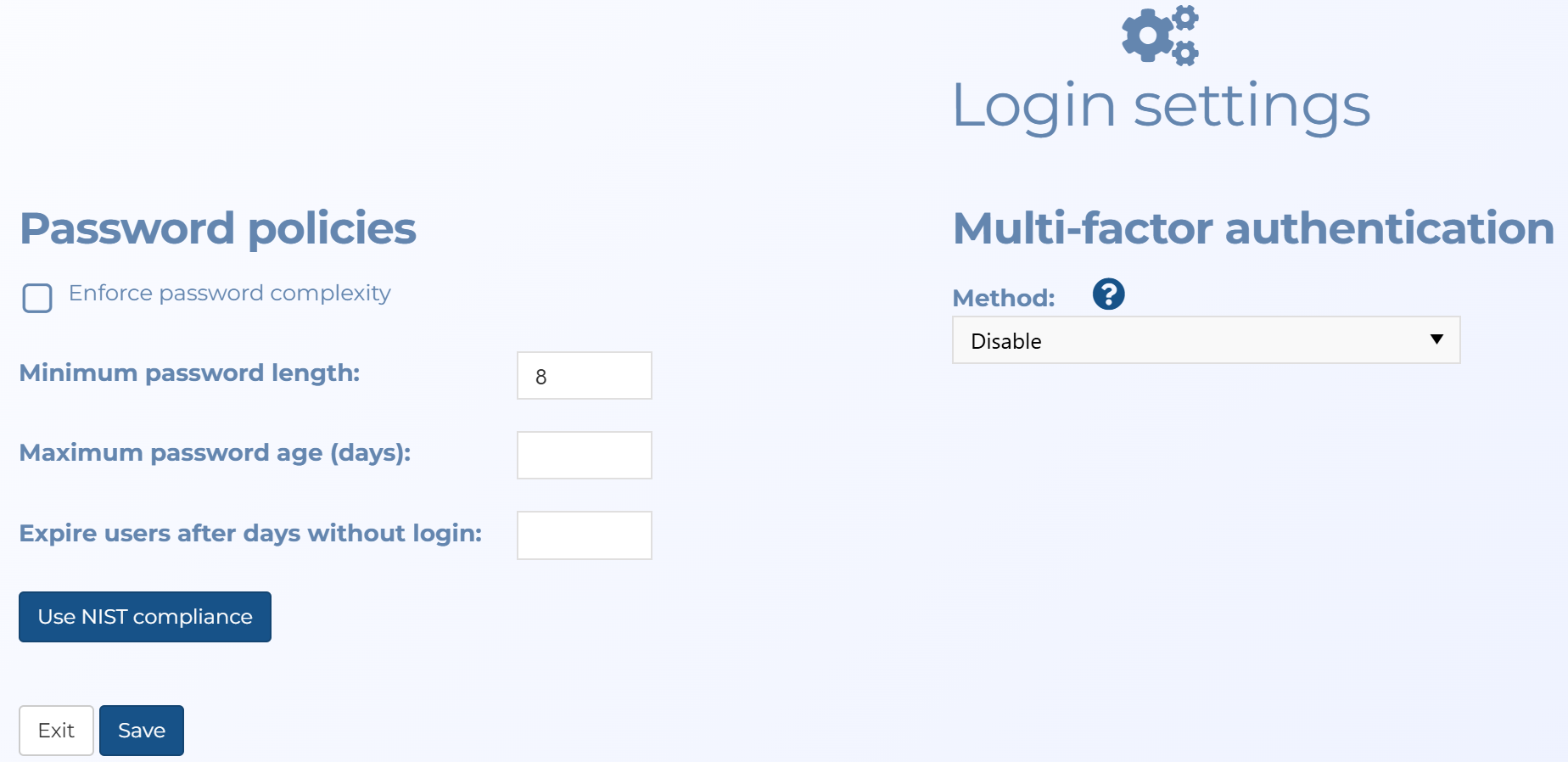
This topic provides an overview of the Login settings screen and all the settings and buttons on it. However if you require step by step instructions refer to Configuring the login security.
Select if you want to enforce password complexity. This means it must:
-
contain a minimum of 8 characters.
-
contain numbers, letters, symbols, uppercase and lower case.
-
not contain number sequence or number repetition. For example, 123 or 333.
-
not contain letter sequence or letter repetition. For example, abC or ccc.
Enter the minimum number of characters required in the password. Note, if Enforce password complexity is selected you cannot apply a value under 8.
Enter the maximum number of days a password can remain valid before a user is automatically notified to change it when they attempt to log in. For example, if you want your users to change the password annually then enter 365.
Enter the number of days after a user last logged in that you want their account to expire. An email is sent to the administrator when the user's account expires. If the user subsequently tries to log in to their account they are forced to change their password before they can log back in, and an email is sent to the administrator.
Click if you want to apply the required National Institute of Standards and Technology (NIST) settings to the account. These are:
-
password complexity is required
-
a minimum password length of 15 characters
-
a maximum password age of 60 days
-
user accounts expire after 90 days of no activity
-
email multi-factor authentication
Select whether or not you want to apply multi-factor authentication to the OSS-ESPA account, and if so the method you want to use. OSS-ESPA's multi-factor authentication requires the user to enter two or three pieces of evidence before they are granted access to OSS-ESPA or the G-Scout App. In addition to their normal password, you can select the following methods for their additional evidence:
-
Disable: multi-factor authentication is not applied and the user only requires their log in password.
-
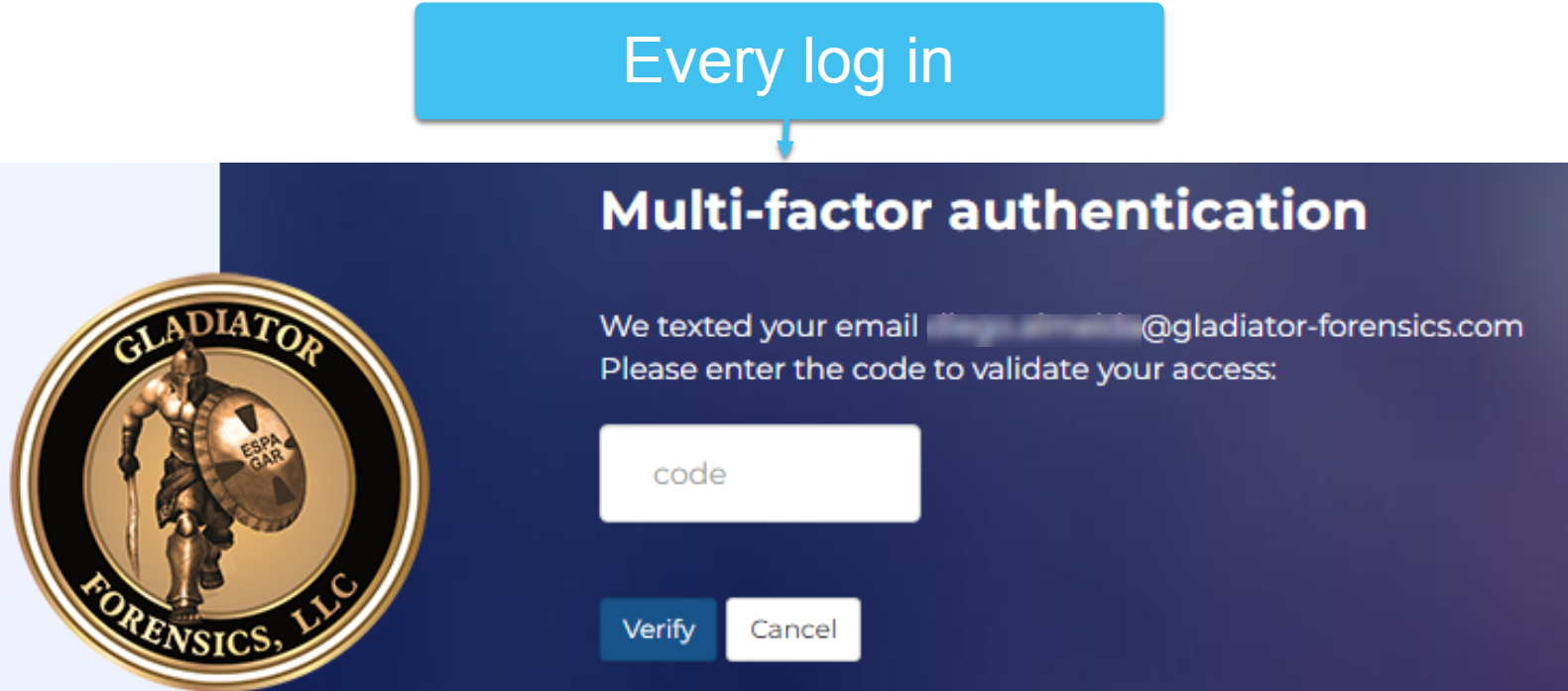
email: at every login, the user must use a code which is sent to their email.
-
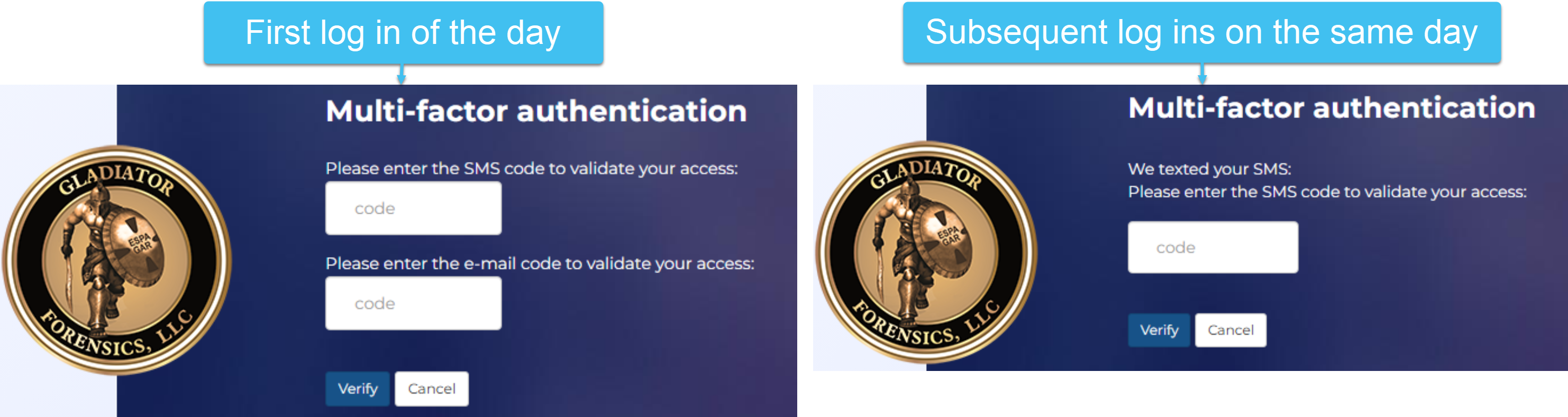
SMS: this setting is used along with Request e-mail validation on first login of the day.
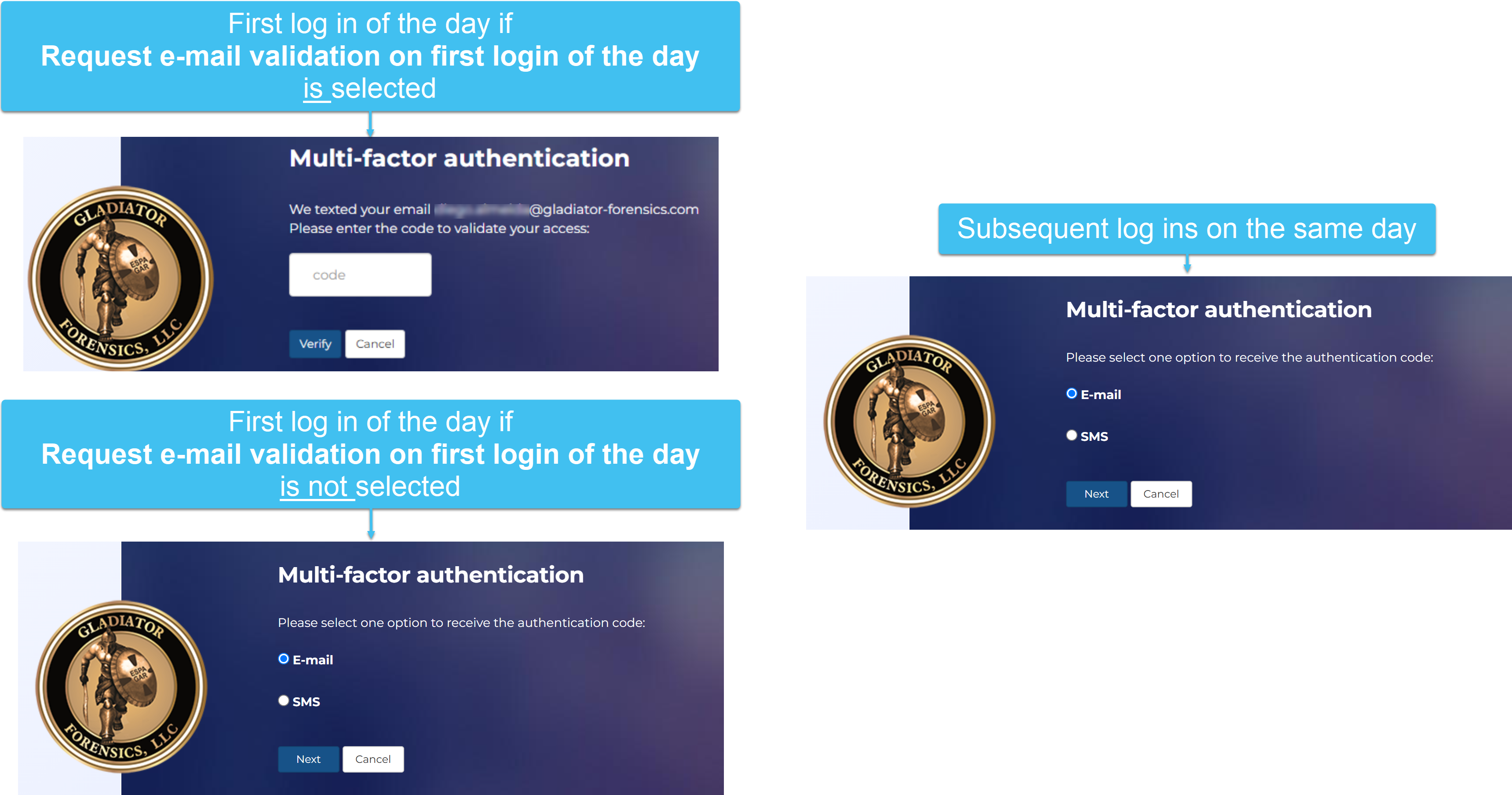
If Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; subsequent logins during that same day request a code sent to their verified phone number.
-
is not selected: all logins request a code sent to their verified phone number.
If their phone number has not been verified then it defaults to email authentication. The user can enter and verify their phone number that the code is sent to using Mobile phone and Verify phone on their Edit user information screen.
-
-
SMS or E-mail: this setting is used along with Request e-mail validation on first login of the day.
If Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; for subsequent logins during that same day they are given the choice of having the code sent to their email or their verified phone number.
-
is not selected: at all logins they are given the choice of having the code sent to their email or their verified phone number.
If their phone number has not been verified then it defaults to email authentication. The user can enter and verify their phone number that the code is sent to using Mobile phone and Verify phone on their Edit user information screen.
-
-
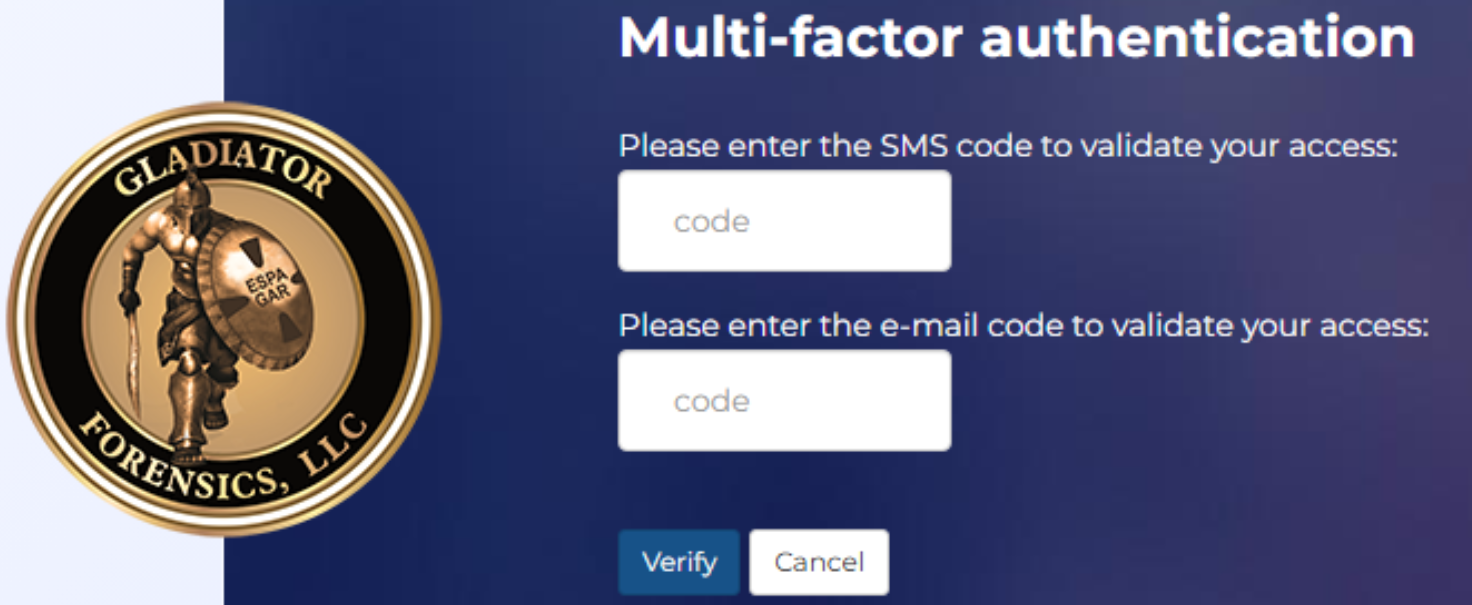
SMS and E-mail: at every login, the user must enter both the code sent to their verified phone number, and the code sent to their email.
If their phone number has not been verified then it defaults to email authentication. The user can enter and verify their phone number that the code is sent to using Mobile phone and Verify phone on their Edit user information screen.
-
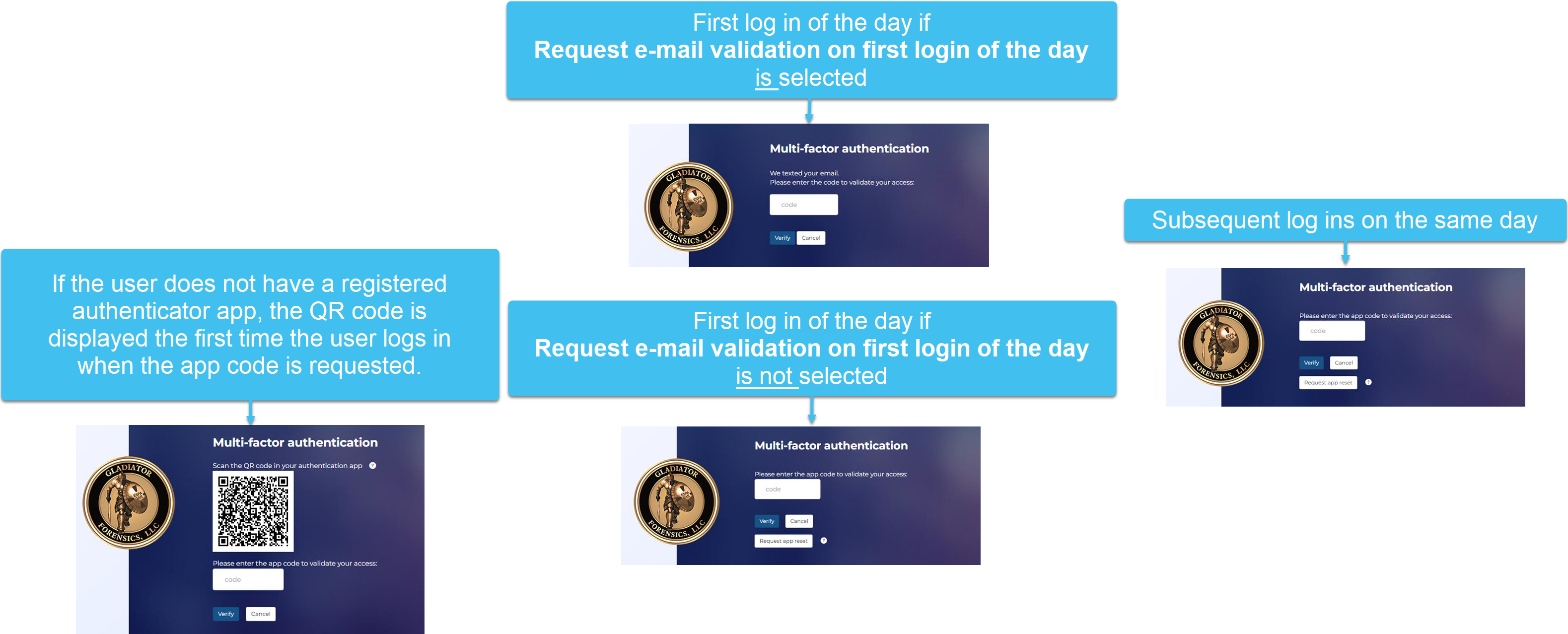
App authentication: this setting is used along with Request e-mail validation on first login of the day.
If Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; subsequent logins during that same day request a code sent to their authenticator app.
-
is not selected: all logins request a code sent to their authenticator app.
-
-
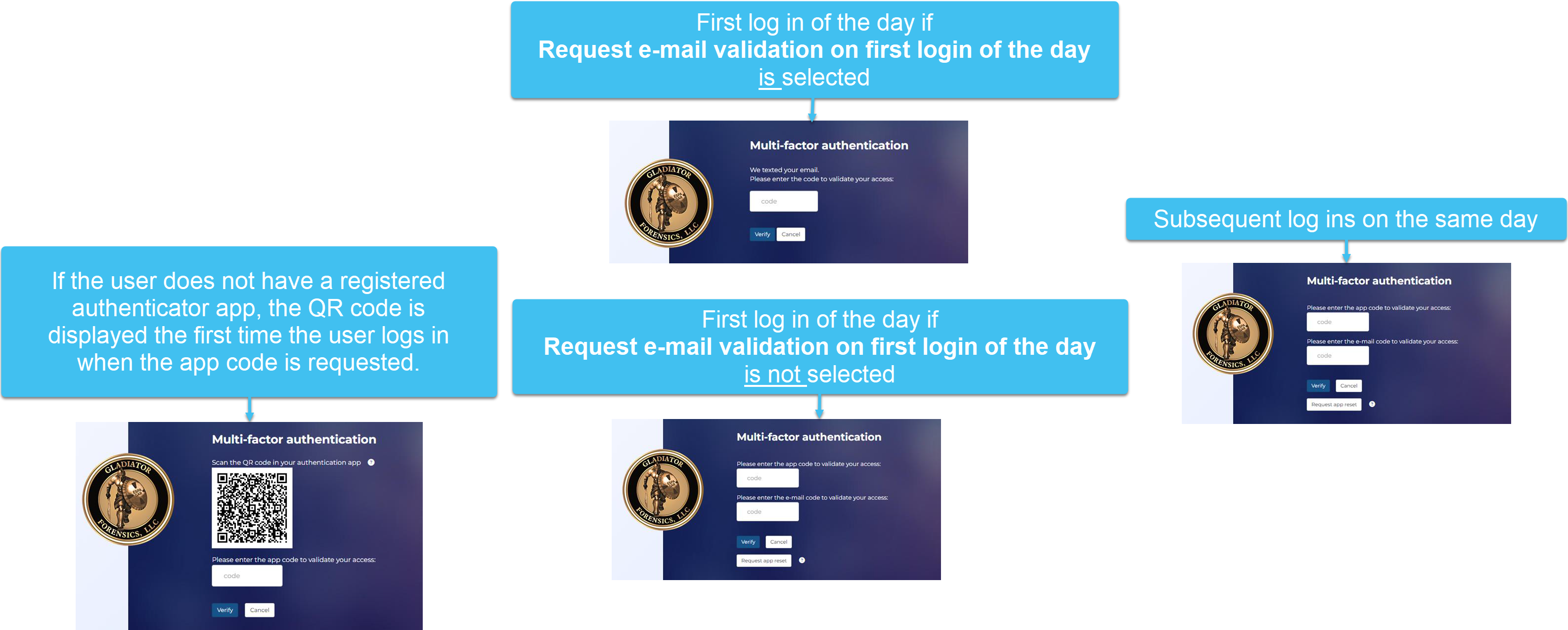
App authentication or E-mail: this setting is used along with Request e-mail validation on first login of the day.
If Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; for subsequent logins during that same day they are given the choice of having the code sent to their email or authenticator app.
-
is not selected: at all logins they are given the choice of having the code sent to their email or their authenticator app.
-
-
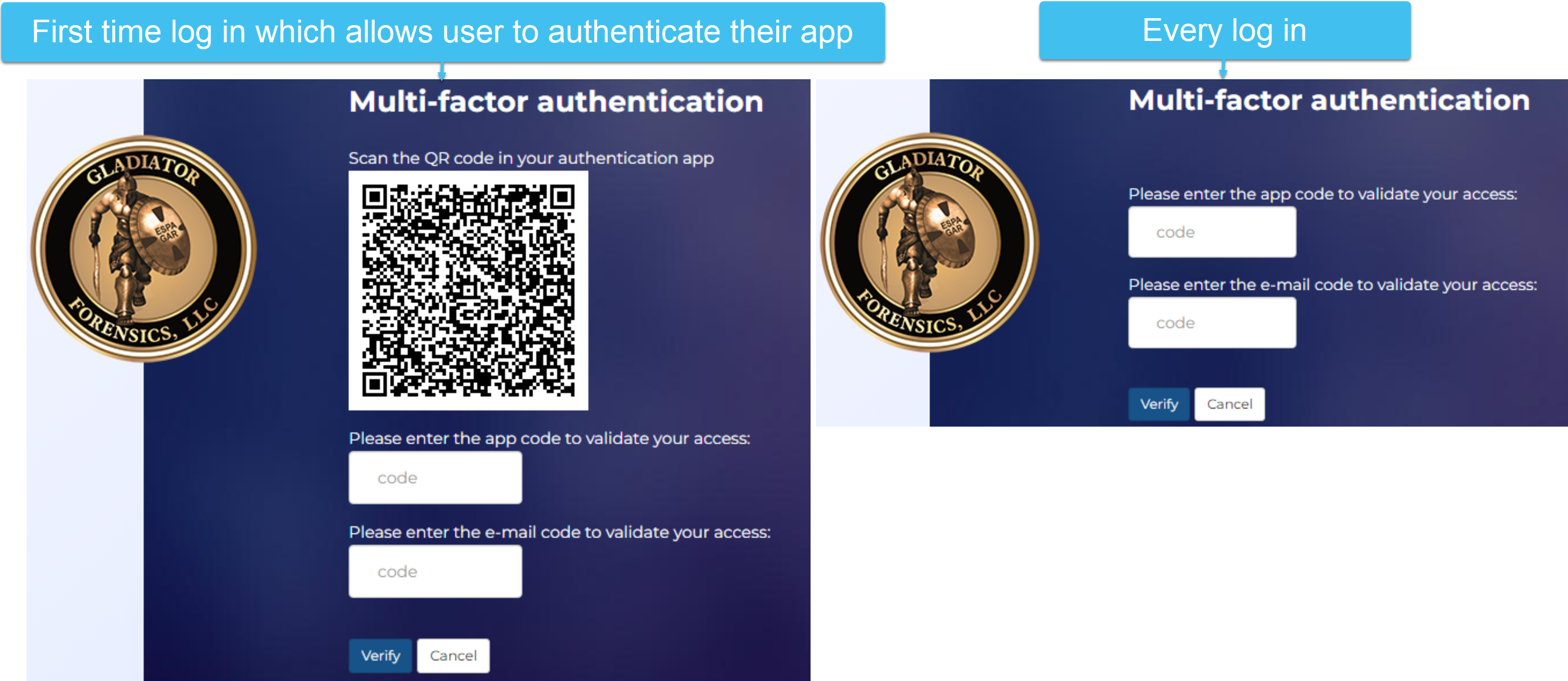
App authentication and E-mail: at every login, the user must enter both the code sent to their app authenticator, and the code sent to their email.
For the app authentication options, if the user does not have a registered app authenticator then a QR code is displayed which they must scan using a supported app authenticator. If the user needs to register another authenticator in the future then you can reset this for them using Reset authenticator app.
Both the Google authenticator and the Microsoft authenticator are supported and are available for download at the following locations:
-
Google authenticator:
-
Microsoft authenticator:
This setting is only available when Method is set to either: SMS, SMS or E-mail, App authentication or App authentication or email.
Select this setting if you always require the first log in of the day to require validation using a code sent to the user's email. This option is useful as it ensures that users whose email account you may have recently disabled but whose OSS-ESPA account is still active, can no longer access OSS-ESPA using just their verified phone number or their app authenticator.
If you normally have this setting selected and your email server is temporarily down, then you can clear the setting temporarily until your email server is restored while still maintaining multi-factor authentication.
This means that if Method is set to:
-
SMS, and Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; subsequent logins during that same day request a code sent to their verified phone number.
-
is not selected: all logins request a code sent to their verified phone number.
If their phone number has not been verified then it defaults to email authentication. The user can enter and verify their phone number that the code is sent to using Mobile phone and Verify phone on their Edit user information screen.
-
-
SMS or E-mail, and Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; for subsequent logins during that same day they are given the choice of having the code sent to their email or their verified phone number.
-
is not selected: at all logins they are given the choice of having the code sent to their email or their verified phone number.
If their phone number has not been verified then it defaults to email authentication. The user can enter and verify their phone number that the code is sent to using Mobile phone and Verify phone on their Edit user information screen.
-
-
App authentication, and Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; subsequent logins during that same day request a code sent to their authenticator app.
-
is not selected: all logins request a code sent to their authenticator app.
-
-
App authentication or email, and Request e-mail validation on first login of the day:
-
is selected: the first login of the day requests a code sent to their email; for subsequent logins during that same day they are given the choice of having the code sent to their email or authenticator app.
-
is not selected: at all logins they are given the choice of having the code sent to their email or their authenticator app.
-